hen we talk about protecting your site, a firewall is considered a necessary and indispensable protection measure. The firewall protects your site from many malicious attacks that may harm your site.
In this article, we will review for you a comprehensive explanation of the firewall, starting with identifying it and exploring its types and how it works, and how to activate it on your WordPress site using one of the easy plugins so that we can help you enhance the security of your site comprehensively.
Explaining Firewall and how it works
The firewall (or firewall) is one of the most important cybersecurity, information and network security tools. It monitors incoming and outgoing internal and external network communications, relying on a set of basic rules to filter those communications that you can control personally to set some additional security standards or He makes some special exceptions, after which he allows connections that comply with the security rules to pass, and immediately blocks connections that he feels threaten the network and do not comply with the security rules.
If we try to simplify the concept further, it is more like a filter that filters all communications that occur on the network, allowing secure communications to occur and blocking malicious communications. The following video explains how Firewall works in an easy and understandable way.
Firewall is divided into two basic types as follows:
- Software Firewalls : These are separate programs that are installed on your computer to secure the network, such as Online Armor and Comodo Firewall.
- Hardware Firewall tools : These are external tools that are connected to the network to secure it.
The importance of firewall for WordPress websites
There are many reasons that show you how important it is to activate a Firewall to protect your site data, and among these reasons are the following:
- The firewall scans all outgoing and incoming connections to external and internal networks to secure you from all malicious attacks.
- Protecting your website from hacking, as if someone is able to hack your website, he may access the data of all customers and control them silently, or he may cause the site to be completely destroyed.
- The firewall prevents remote access points to your device, as some hackers currently rely on complete control of your device by accessing those points and they transfer and delete files without being monitored, and only disconnecting the network from the device and fixing those points with separate protection programs will stop them.
- The role of firewalls is not limited to spyware files only, but also works to stop viruses from reaching your device, and most firewalls can successfully stop the famous ransomware virus.
- Firewalls secure the connection points on which most modern online games depend.
- The firewall also secures your bank account data and all sensitive accounts that you rely on on your site.
A firewall may consume part of the server’s resources, causing slow network and data transfer, but the minor damage resulting from these types is much less than the damage you may suffer when a hacker succeeds in entering your device and spying on it or controlling it, so we never recommend turning off a firewall. Protection as some recommend.
Types of firewalls
There are 5 basic types of firewalls, and all of them work to prevent malicious attacks, but the way each type operates differs in its configuration and in the way you block malicious attacks. Therefore, the types can be divided into the following:
1. Packet Filtering Firewalls
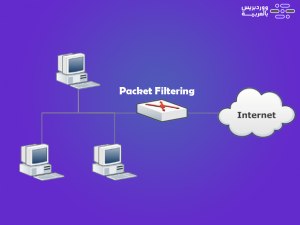
This type is one of the oldest types of Firewall, and one of the best types that you can rely on for its speed and quality in checking communications, as it forms an external checkpoint that collects all the information issued by the server from the IP number, connection type, access gateway number, etc.
After that, it compares them to its security standards, and if they pass this analysis, it allows direct communication, but if they do not pass this analysis process, the contacts are prevented from completing the connection to the network.
2.Proxy Firewalls
Proxy Firewalls also come from the older types of firewalls and are known as a proxy firewall, which is an intermediary between internal and external networks and the Internet, as the name suggests.
For example, if you search on Google for the meaning of firewall, your device will request information from the Google server directly, but when using Proxy Firewalls, it will obtain this request and redirect it on the basis that it is coming from it and not from the device directly, and therefore the Google server cannot Knowing the real identity of your device, your geographical location, or collecting any information about you because the information he will obtain will be from the fictitious intermediary.
3.Next-generation Firewalls
Next-generation Firewalls It is known as the second generation firewall and is symbolized in most references by the abbreviation (NGFW), and it is one of the best firewalls that many major companies rely on.
This protocol examines incoming and outgoing connections from the Internet more deeply, as it examines all incoming connections from the server, and contains some modern technologies such as IPS technology that protects you from viruses and malicious attacks and automatically filters spam.
4.Circuit-Level Gateway
Circuit-Level Gateway is a traditional firewall that is very fast and does not consume a large portion of the device’s basic resources when working. It relies on forming gateways that examine the TCP protocol, which is a protocol used to transfer data across networks and ensure that it conforms to its security standards.
5.Stateful Inspection Firewalls
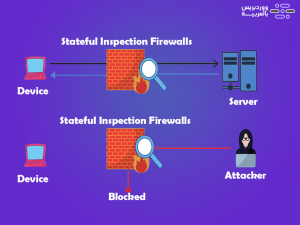
Stateful Inspection Firewalls is known as an inspection firewall, and it is also a type of traditional firewall, as it monitors outgoing and incoming traffic and filters it automatically based on the security rules prepared in advance by the user, but it is distinguished by monitoring the connection from the first moment of connection until the site is closed. Completely.
This method relies on the filters resulting from old connections to the same server to prevent new connections, so it must be updated continuously, and it checks the TCP protocol as well, so it constitutes very strong protection, but it consumes a large portion of the device’s basic resources when scanning, which causes slow speeds. Transferring data over networks.
Read also: Protecting your WordPress site from all vulnerabilities and attacks | Comprehensive guide
Activate Firewall on your WordPress site
There are many plugins that can be installed on your WordPress site in order to create a strong firewall that protects you from malicious attacks, and one of the best of these plugins is the All In One WP Security & Firewall plugin because it constitutes a large group of protection tools that includes the firewall.
In order to install the plugin on your site, you will go to your WordPress control panel, then go to the Add-ons tab and choose Add New , then type in the search box: All In One WP Security & Firewall in the search box, then choose the tool and click Install Now .

The plugin will be installed within seconds, then you will click the Activate button . ( Read also: How to install a plugin on WordPress )
Then, after installing the plugin, you will find a new tab called (WordPress Protection) in the side menu, which you need to click on and choose Firewall, as in the following figure shown:

After that, you will enable the option to enable basic firewall protection, which in turn will block access to htaccess and the wp-config.php file , and this will not affect the operation of either file.

After that, it will automatically apply a maximum file upload limit that does not exceed 10 MB, but you can modify it by controlling the Max File Upload Size box, and the basic unit is the megabyte.
The third step is to activate the option to completely deny access to XMLRP and the option to disable the Pingback notification function in XMLRPC. This is because the xmlrpc.php file contains many security vulnerabilities such as the XML-RPC API, which hackers rely on to hack sites and copy files from the site automatically, which increases Click on the website server.

Then activate the option to deny access to the debug.log file, as this WordPress automatically saves the debug log in this file, which may contain some important information that hackers may be able to exploit.

The final step is to click on Save basic firewall settings to save all previous options.

questions and answers
There are some questions that may come to your mind when using Firewall, including the following:
- Which is better, Hardware Firewalls or Software Firewalls?
Hardware Firewalls are better than Software Firewalls for two reasons, which are as follows:
- Hardware Firewalls are set up once on the entire network and do not need to be installed and set up on a separate network device like Software Firewalls.
- Hardware Firewalls do not consume a portion of RAM or CPU, unlike Software Firewalls, which consume a portion of both.
- Can more than one Firewall be used at the same time?
Yes, it is possible. In fact, it is better for you to use more than one firewall at the same time. It is like forming a line of defense with another line of defense behind it. If the first line of defense is breached, you find another line of defense that protects the network from harmful attacks.
Thus, we have reached the end of our article in which we explained the explanation of Firewall, its most important types, and how it works to secure your website, and how to add Firewall to protect your WordPress site in a simple way. In conclusion, we can say that the firewall is considered one of the simplest and most important tools for protecting the site from hacking and spyware, so we advise you to install it now. on your site and protect it from any hackers or saboteurs.
If you have another question or problem related to using the firewall in WordPress, write it in the comments section, and we will answer it as soon as possible, God willing.
































Leave a Reply