The task of securing and protecting your WordPress site comes as a necessary task and one of the highest priorities of website owners, because any breach in one of the security elements may lead to the loss of sensitive data on your site or the complete collapse of your site, which means incurring many losses, and despite the fact that WordPress itself as a system Content management is highly secure, but the presence of huge numbers of templates and plugins spread across the Internet may pose a potential threat to your site.
Your WordPress site can be secured by taking many measures in terms of security settings, whether in terms of the administrative decisions you make as a site manager or in terms of the tools and technical environment you rely on on your site, and this is what we will talk about in detail in the article.
Basic steps to protect your WordPress site
1- Choose secure hosting
The security and stability of your site begins with choosing a reliable hosting company, as it is necessary to host your site on secure servers, which means the security of the sites hosted on the server, and vice versa as well. It is important that you carefully choose the service provider that you will rely on to host your site , and there are some specific criteria that must be taken into consideration regarding the hosting company’s security standards, which are as follows:
- Operating System Security
The security of hosting companies’ servers starts with using a secure operating system. Therefore, you must ensure the security of the hosting company’s operating systems, whether (Windows or Linux), and provide continuous updates, security, and protection. You must also make sure to provide modern copies of the software files on the server, such as updating PHP files periodically.
- SSL Certificate The SSL security certificate
is one of the most important factors that helps in choosing the most secure hosting company, as ensuring the availability of the security certificate with the hosting company would contribute to securing the connection between your site and the visitors. Browsers also add a “green lock” symbol, which is considered an important security sign for most website visitors
- Backup & Restore Support
If your site crashes completely or you lose part of its files, in this case it is necessary to have a backup copy of the site files to be able to restore them. You’ll need to make sure that your hosting service provides good, stable backup systems that help your site stay secure on an ongoing basis.
Therefore, when choosing a hosting company, you must ask about the possibility of storing complete backups of your site on an ongoing basis, and you must also ask about the period of time that backups of your site remain on the company’s servers.
- Firewall Protection System:
One of the most dangerous attacks that may infect your site are DOS-type attacks that can easily infect your site if the hosting company does not have a Firewall Protection system that responds to these attacks that have destructive effects. Therefore, make sure that the hosting company has a strong firewall system and is updated periodically and continuously.
2- Activate two-step verification when logging in
Two-factor authentication is a security feature spread on many popular sites with the aim of adding an additional layer of protection to your site’s login data. The idea in brief is that when you try to log in to your site, a phone confirmation code is sent and the user is asked to write this code on the login screen, so that the login is confirmed.
One of the most popular add-ons that does this is the Google Authenticator add-on , which creates a two-step verification system to log in to your site:
Once the add-on is installed and activated on your WordPress site, you will be asked to download the Google Authenticator application from the Play Store, Apple Store, or Windows. Then, after downloading the application, you will scan the QR code that appears in the add-on settings on your website, and an activation code will be sent to you on the application, which you enter in the designated box within the add-on settings page, thus activating two-step verification automatically.
After that, anyone who tries to enter your site, even if the login data is valid, will send the login confirmation code to the site owner in the Google Authenticator application, which will show a notification or alert to the site manager containing the login confirmation code, and thus no one can log in except After checking the sent code.
3- Register via email instead of a username
When you or any member of the site logs in, you must enter a user name and password. In this box, it is recommended that the email be placed in the user name box instead of a user name consisting of a few letters.
This step helps reduce the chances of guessing the login data because the email is more difficult to guess than the username, which consists of a small group of numbers and letters.

4- Log out of inactive members of the site
If a site member logs in to one of the devices, then leaves the device he is using, and a hacker obtains that open data in front of him, then the site is under potential danger!
Therefore, one of the WordPress site security options is to log out members who have passed a certain period of inactivity on the site, which is known as session timeout. You can do this by adding Inactive Logout

After installing and activating the add-on, the add-on control panel will open for you, in which there is a section to add the specific time to keep the member logged in before logging him out, which is what the first arrow shows, where you can specify 10 minutes for the member to be inactive, and after the time has passed, he will be logged out automatically. .
Also, the second arrow indicates the message that appears on the screen after logging out the inactive member:

Note: The previous procedure is completely useful and appropriate if there is a large number of members on your site, but if the number of members is few and they are trustworthy people, there is little need to do this procedure.
5- Beware of purchasing templates and add-ons from unknown sources
Pirated templates or so-called Nulled themes and plugins have spread, the licenses for which are broken and republished online at a low price or sometimes for free. Some beginners think that this behavior of the hacker is for a charitable purpose 🙂
Often times, the way is made easier for hackers to implant malicious codes inside your site that will change the site’s behavior or completely steal data, through these plugins and templates. Therefore, be sure to purchase templates and add-ons from the program’s official store or through trusted stores only.
The best security plugins for WordPress
When talking about protecting your WordPress site, using an efficient security plugin is essential to help automate security measures. Let me tell you the 4 best security and protection plugins for WordPress that will help you with these tasks:
1- Add MalCare Security
The MalCare Security add-on provides multiple security options for the site, starting with securing the login attempt and blocking suspicious IPs. Securing site files to protect them from hackers trying to access and modify them. The add-on also provides backup services, through which it is possible to automatically activate updates to WordPress files, as well as update templates and plugins to the latest version, in addition to providing scanning services for internal site files when they are found. Suspicious or questionable files that the extension deletes before affecting your site.
2- Add Sucuri Security
The Sucuri add-on is considered one of the most popular security add-ons that provides complete statistics about the security and health of your site on an ongoing basis, and allows activating automatic site scanning to track suspicious operations within the site and block them immediately. What also distinguishes the add-on is that it contains a tracking system that can detect suspicious changes in your SEO settings. By archiving your site on Google and making any modifications to the search words or injecting links with words that will steal visitors.
The add-on also contains a strong firewall to deal with dangerous attacks, and you can create a blacklist that contains the addresses that you want to block from browsing or visiting the site.
3- Add All In One WP Security & Firewall

The All in One WP Security add-on provides many options for securing the access of all members to the site, as you can view the IP addresses through which members accessed the site and alert you if a member’s data is registered through a different or suspicious IP.
It also provides a system to protect login with a large number of random passwords and work to reduce them.
4- Add Wordfence Security

The Wordfence add-on is also a reliable add-on that provides many security options that greatly enhance the security of your WordPress site. It counters random login attacks through passwords that are guessed using suspicious programs. The addition provides activation of the two-factor authentication system, as well as the famous CAPTCHA system to secure the login process.
Watch: Explanation of installing and configuring the add-on on your site
Note : After reviewing these add-ons and the information that we explained to you and clarified from their reliable sources, you can choose from among them, as you choose one add-on in which you find all the insurance options you are looking for and install it.
Do not install too many security plugins to your WordPress site because the presence of many plugins that perform the same task may lead to a conflict in the work of these plugins.
Advanced steps to increase the security of your site
Now that we have learned about some simple tips and procedures through which you can improve the security of your site without the need for any programming experience, and this is what we will talk about in the following paragraphs, we advise you here that it is important to make a backup copy of the site before adding, deleting, or modifying it. Any of the code within the site, and ensure that all the mentioned modifications are made accurately.
1- Keep the config.php file in a safe state
The config.php file is one of the most important files related to the security of your WordPress site. As this file contains the most highly sensitive data and information regarding the security of your site, and when you try to access this file and make modifications to it or steal its data, your site is very simple steps away from harm. You can view a comprehensive guide regarding the config.php file and ways to secure it .
2- Canceling the ability to modify the site’s files
On a WordPress site, it is possible to add more than one person as a site manager, who can access the site’s control panel and make changes. By default, any admin on the WordPress site can access the template and plugin files and modify their source code. Therefore, it is important that you remove the ability to modify site files by other managers. To do this, you can open the wp-config.php file and write the following code inside it:
3- Canceling the site’s files from being displayed by visitors. Directory listing
When you access your site’s file manager, and create a folder called “Data” and upload some important files into that folder, then you do not create an index page inside the folder to display it to visitors, in this case any visitor will enter the folder path via www.example.com /data can view all the files inside the folder and possibly download them as well.
To protect your site from this error, you must add the following code into your site’s .htaccess file, as this code prevents visitors from opening and viewing the site’s files:
4- Block external hotlinking of your site images
The term Hotlinking refers to an external site accessing a site and copying some image links that are in the form: www.example.com/image.png . Whoever places the link to the images inside his site, and thus the images appear on his site, but they are hosted on your site. What does it mean? this ?!
This means that every time that image is displayed on the other site, it is called from your site first, and this causes a drain on your site’s server resources, and thus a huge number of your site’s files may be called in this way, causing the site to crash or be exposed to damage.
To prevent your site’s images or files from appearing or being retrieved from external sources, you must disable this command, and the easiest way to do this is by using one of the plugins that do this, the most famous of which is the All in One WP plugin.

You can also disable Hotlinking queries without plugins by blocking Hotlinking from within the .htacess file .
5- Change the prefix of tables in WordPress databases _WP
When you install WordPress on your site, it creates a large number of tables within the server databases, and these tables often begin with the word WP_, which makes attackers easily predict the names of the targeted tables that contain all WordPress data.
So you should change those characters to different letters and symbols:
You can see a full explanation of how to change WP_prefix to WordPress tables .
6- Take backup copies of your site periodically
Any website on the Internet is vulnerable to damage or disruption, even temporarily. In some cases where your website is exposed to disruption or the loss of some files, it is necessary to have backup copies of the website’s files and data before losing that data.
See the comprehensive guide to making website backups and the best ways to secure them .
7- Change the default data to log into Cpanel

Immediately after purchasing hosting for your site, the login data is sent to your site’s control panel (Cpanel), and therefore we advise you to change the default data that is sent by default after purchasing the hosting to increase the security of access to your site.
8- Hide the WordPress version number
It is very easy to obtain the current version number of WordPress on your site, as it can be accessed through the site’s source code or in the site’s control panel for all registered members of the site. If hackers get the version number of WordPress you are using, it will be possible to design malicious programs and codes to affect your site, because they know the vulnerabilities of the version you rely on.
To hide the WordPress version number only, you can add the following code to the functions.php page:
function wpbeginner_remove_version () {
return '' ;
}
add_filter ( 'the_generator' , 'wpbeginner_remove_version' ) ;9- Prohibiting the operation of PHP-type software files
Vandals often use PHP language codes to create malicious software files that contain a number of commands that can disable certain parts of the site or even steal important data in databases. Therefore, it is important to disable running php files in places that do not need files of this type.
One of the most famous paths in which there is no need to have PHP files and which must be disabled from running this type of file is the Uploads/ folder within the WordPress website file manager.
You can open the .htaccess file. And put the following code inside it to block any php files from running on your site:
< Files *.php >
deny from all
< /Files >For more information, you can see ways to modify the .htaccess file correctly.
10- Hide the wp-config.php and htaccess files from appearing in the file manager
To add additional layers of security, you can hide the wp-config and htaccess files from appearing in the file manager, but they will still function properly within your site.
You can hide the wp-config.php file by placing the following code in the htaccess file. :
< Files wp-config. php >
order allowed, deny
deny from all
< /Files >htaccess file can also be hidden by placing the following code in the htaccess file. :
The most common hacking attacks that occur and how to confront them
Here is a list of the most important vulnerabilities that exist in WordPress as a content management system, how hackers can exploit them to penetrate your site, and how to fully protect your site from these types of attacks:
- Backdoor sneaking
- Pharma Hack Attack
- Brute-force attacks Login Attempts
- Malicious Redirects vulnerabilities
- Cross-site Scripting (XSS) vulnerabilities
- Denial of Service attacks
- WP-VCD.php Hack Attacks
- Phishing attacks
- Japanese keyword hack attacks
These are the most famous attacks or vulnerabilities that hackers exploit to harm your WordPress site. Let us now talk about them in more detail and how to confront them:
1- Backdoors
Backdoor hijacking is one of the most common ways hackers and hackers use to harm your site. This type of attack is carried out by planting suspicious files within the WordPress files themselves, often within the famous wp-includes path, and they are also planted in different places.
This attack comes primarily in terms of exploiting weaknesses in the hosting company in which the site is located, as hackers can plant a backdoor file in all WordPress sites located on the same hosting company if they succeed in penetrating the company.
Hackers often plant these malicious files through which you can control very large parts of your site and possibly steal important data, and sometimes disable and sabotage the entire site if this vulnerability is not discovered by the site owner. These are the most popular places where these types of files are downloaded:
- Template files
Template files are very vulnerable to these types of malicious files being planted inside them, due to the lack of interest of some users in updating their templates as well as the lack of a firewall, so we always recommend updating the effective templates on the site to the latest version, and using safe templates.
- Plugin files
, like template files, can have backdoor files installed inside them. We also recommend that all active plugins on your site be secure and constantly updated. We also recommend deleting any inactive plugin on your site, as well as paying attention to installing one of the plugins that creates a firewall for your site.
- Uploads path:
The Uploads folder is also very vulnerable to this type of file being planted, because this folder contains a large number of image, video, and other files, and therefore it is difficult to discover suspicious files inside it, so it is recommended to secure this path as we explained in the previous steps.
- The wp-includes folder
is one of the places that hackers most exploit to plant Backdoor files inside it. If the matter succeeds and the malicious files are planted inside it, your entire site files can be stolen by accessing the login data to your site or files containing the login data to the administrator. Files or Cpanel. Therefore, one of the security measures is to change the path of the wp-includes folder .
Now that we’ve looked at how hackers plant Backdoor files inside your site, we’ll now talk about ways to protect against these types of attacks.
Certainly the only solution to repel Backdoors attacks is to discover the location of these files and completely delete them from the site. But it will be difficult to do this task manually by searching through thousands of files on your site, so you can use some WordPress plugins that do this task, as they search within the site’s files as well as databases, and when they find a strange file that was planted or suspicious activity on your site, they It alerts you immediately and takes the appropriate decision to protect your site.
You can use any of the plugins that do this task, the most popular of which is Sucuri Security.
2- Pharma Hack attack
It is considered one of the most famous attacks carried out by hackers in order to benefit from the links to your site that appear in search engines. You may have noticed one time when entering a site from a search engine and discovering that it opens a link that is completely different from the link that appears in the search engine.
This attack was called Pharma Hack because it is used to sell illegal drugs by hacking some sites that appear in Google search, for example, and implanting some malicious codes that force the search engine to direct the visitor to a link completely different from the original site link. There are advertisements for medicines, illegal drugs, and other unauthorized products without the prescriptions of a doctor or specialist.
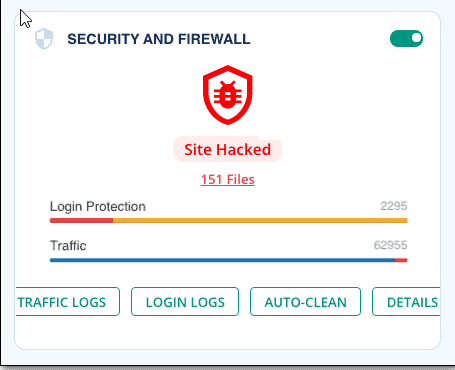
Notice the previous image showing a security add-on that detected a site being hacked and files stolen.
This attack is not intended to harm the victim’s site in most cases, but rather its only goal is to exploit the appearance of some links in Google search to sell unauthorized products.
Although it is a heinous attack that is extremely harmful to your site, detecting it will not be completely difficult for you if you have some malicious file detection tools on your site, such as the Sucuri Security add-on.
Which we referred to above. The add-on alerts you immediately if it detects backdoor files, which are the ones through which the pharma hack vulnerability codes are planted. All you have to do is install the suspicious file checking plugin and initially delete any strange file that is detected.
3- Brute-force Login Attempts
These attacks are also called brute force attacks that may hit your site, as attackers use some programs that try to guess passwords through tens of thousands and perhaps millions of guesses in a very short time.
Although they may be destructive attacks on the site, they are very easy to confront and can be prevented with some steps that we have summarized in the following points:
Change the login path to your WordPress site’s control panel
By default, the login path to your site is as follows: example.com/wp-admin. Hackers know well the famous path to enter the site’s control panel, which is the place where the username and password are placed. So changing the name of this path wp-admin to a different name makes it very difficult to predict the path to enter the control panel. You can change the name of the login path to the Control Panel using the Hide Login add-on

After installing and activating the add-on on your site, you can enter its settings, where you will find the login URL option in which you can write any text to be the entry path to the site’s control panel instead of the famous and well-known wp-admin path:
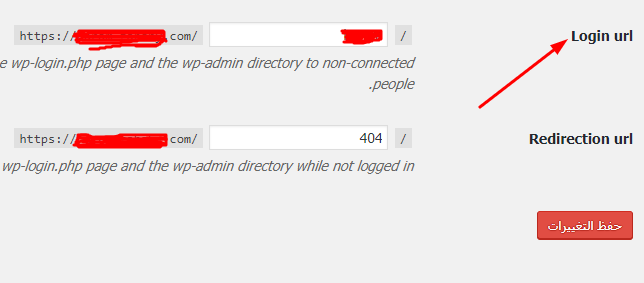
You can also block certain IPs from entering the WordPress control panel login page, by entering the .htacess file and adding the following code:
AuthUserFile /dev/ null
AuthGroupFile /dev/ null
AuthName "WordPress Admin Access Control"
AuthType Basic
< LIMIT GET >
order deny,allow
deny from all
allowed from 11.11 . 11 . 111
">You can see more details about blocking hapes in the .htacess file
Use a strong username and password

Stay away from using the popular username Admin or easy passwords, for example: password123 and anything similar to these very easy inputs that many guessing programs can easily recognize. The username should be fairly long and contain numbers and special symbols such as ($ – # – @ *), as well as the password. Make it as difficult to guess as possible. The more time you take to choose a completely unique password and username, the further away you will be from Brute-force Login Attempts attacks.
Make it difficult for hackers to guess your username :
Do you use a username that matches your profile name on the WordPress website?! So, you are making it easier for attackers to guess your username when they see your profile name that appears on the blog page under any published article. To change the profile name, go to “Edit my profile” as in the image above, or “edit my profile” and change the profile name to be different from the user name to enter the WordPress control panel.
Set a maximum limit for attempts to access the control panel
It is considered one of the security practices that you can implement on your WordPress site to prevent attackers from entering the site’s control panel. You can set a limit on login attempts using the limit login attempts plugin.
4- Malicious redirects vulnerabilities
Malicious redirects are considered one of the most serious infections that your site may be exposed to, as this vulnerability adds codes that redirect your site’s links to another site’s links. This could be due to traffic being stolen from your site or the site’s reputation being completely destroyed. This vulnerability may cause Google to lower your ranking in the search engine, or perhaps the site disappears completely. It may also cause the website server to be blocked by the hosting company due to the large-scale link conversion process that is classified as “suspicious behavior by hosting companies.”
Simple steps that reveal if your site is infected with the Malicious Redirects vulnerability :
- If some or all of your site links redirect to another domain.
- If your site sends notifications to visitors without you doing so.
- If Google has classified some of your site links as “suspicious” or Spam.
- If you discover suspicious codes inside the index.php file.
- There are a number of suspicious files inside your site’s file manager.
- If your .htaccess file contains strange and unknown codes. htaccess file guide and how to protect and secure it.
How to prevent Malicious redirects vulnerability
When infected with this vulnerability, it cannot be eliminated by deactivating some strange add-ons on your site, taking a backup copy of the site, or even updating the add-ons and templates to the latest versions. The guaranteed and effective solution is to install an add-on that protects the site from these redirect codes.
The Marcare add-on is considered the best option to get rid of this highly damaging vulnerability to the site, but it is a paid add-on, and in the event that you are infected with this malicious vulnerability, do not think that using any scanning or scanning add-on for your site may be able to get rid of that loophole with a free add-on.
5- Cross-Site Scripting (XSS) vulnerability
In this type of security vulnerabilities that affect poorly protected sites, malicious codes are planted inside your site, and then using those codes, the mail account is manipulated and thus emails are sent to visitors and users of the site or application, as these messages contain malicious codes from It would steal cookies files located inside visitors’ web browsers, as these files contain the login data for visitors and users of the site, and thus it is possible to enter the site and manipulate customer accounts using the login data that was stolen using this vulnerability.
Types of XSS vulnerabilities and ways to protect against them:
In order to understand more about the extent to which this vulnerability negatively affects the site, here are the types of this vulnerability, and then we will discuss how to protect and respond to it.
- Indirect attack (
reflected This data is then processed and used to steal the victim’s login data to the site, and thus his account on the site can be accessed using that stolen data.
- In the second type, the direct attack ( persistent The files are transferred to a different domain, which is controlled by hackers, and thus they obtain cookie files that contain visitors’ login data to the website, and thus control their accounts through the website.
As you can see, this vulnerability does not only negatively affect the security of the site itself, but it also affects the security of visitors and users of the site, stealing their data, and carrying out illegal operations using that data.
Getting rid of the XSS vulnerability.
Of course, you can manually inspect your site files to delete any suspicious files or codes, but this will take you a lot of time and effort and may make it difficult for you to access them, but in return you can use any of the WordPress plugins that do this for you. The most famous of these additions is Sucuri Security , which we mentioned before. When it detects a vulnerability, it sends you an alert and gives you the option to delete suspicious or untrusted files from your site.
6- Denial of Service attacks, or what is known as DOS
It is one of the most common security vulnerabilities or threats that cause the entire website to crash and stop, and it is also called (denial-of-service attacks), as this attack primarily targets the efficiency of the server on which the website is hosted, where many malicious programs are used that send a huge and intense number of From fake visitors to the site, thus exhausting server resources and could cause the entire site to stop.
This vulnerability has a bad history in the world of information security, as it was the largest DOS attack in the world in the year 2016, in which attackers sent DOS attacks to the most famous and largest international websites and caused the websites of the largest companies such as Facebook, Amazon, PayPal, and Instagram to crash. And dozens of other websites that were disrupted due to this vulnerability.
Prevention of DOS attacks
Methods of protection from these attacks vary, as there are methods that are highly effective and others that are effective with some reservation. However, the best and strongest solution is to choose a hosting company that provides protection from DOS attacks, as the hosting company that has protection systems against DOS attacks is the best choice for Here’s how to protect your site from this vulnerability.
Another thing that helps protect against DOS attacks is to disable the xmlrpc.php file. You can see how to disable it in the htaccess article. This is because this file is what allows third-party applications to send data to your site and interact with it, which can be exploited to send DDoS attacks.
7- WP-VCD.php Hack attacks
Another type of sabotage attack that affects some WordPress sites. In this type of attack, hackers access the site’s control panel as well as internal file paths, and store unauthorized files such as files that contain software license crack data and other files that are stored. on your site and call it anywhere else for the purpose of downloading it illegally, which negatively affects your site’s hosting resources, and may also expose your site to being blocked by the hosting company.
Such attacks can be prevented by using one of the firewall add-ons that we talked about previously.
8- Phishing attacks
In this attack, hackers exploit weak points in the WordPress site, which could be in some plugins or templates that are not updated, and plant malicious codes in the site’s links and obtain full access to the site. The site’s mail account is exploited to send emails to thousands of users containing links aimed at stealing data or bank card numbers, etc.
Also, confronting these types of attacks will be through the use of a powerful firewall program, represented by any of the add-ons we mentioned.
9- Japanese keyword hack attacks
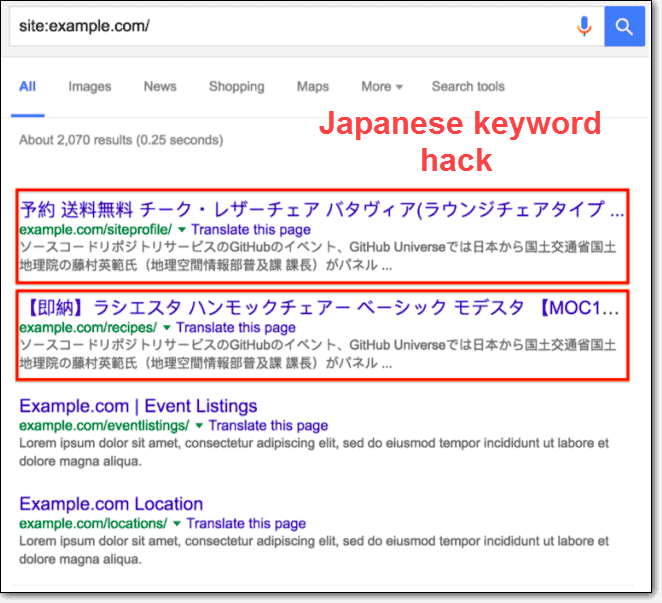
This vulnerability is one of the vulnerabilities that have spread recently, as it works on the same principle as the previous vulnerabilities, and it attempts to find weak points found in some plugins or templates on the WordPress site, and begin exploiting them to plant malicious files and codes that replace the links and texts of the site pages with words in the Chinese language. This is with the aim of the site appearing in search engines based on the names of products in the Chinese language, and thus they place links to purchase those products within the victim’s website, taking advantage of the site’s old domain, which may be highly trusted by Google.
Also, the protection add-ons we talked about can be used to confront this type of attack.
Conclusion|
In the end, as you followed us on our journey during this article, we talked about the most important risks that your site may face, as well as the most important tips for securing the site and protecting it from any possible attack. Just as there are many WordPress plugins that help you set up security options within your site, the security behaviors and measures you take on your site are the most important, whether in distributing permissions, using malicious files, securing your personal account, etc
































Leave a Reply