ou may have heard before about a brute force attack, and you are still searching for the best security measures to protect your site from these sabotage attacks, which may cause the complete destruction of your site.
We had previously talked about the most famous attacks and how to confront them . Today, we are highlighting this type of attack that may exploit some of the weak points on your site to infiltrate inside and do many things that would exploit your site’s hosting resources. Also, the attacker can exploit accounts. Email to send misleading messages to users with the aim of stealing their data.
In this article, we will learn about the brute force attack, which is one of the most common attacks among website owners. We will highlight the most important vulnerabilities that hackers can exploit in order to infiltrate your site. We will also show you the most important security practices that can be taken in order to fully protect a site.
What is a brute force attack?
A brute force attack in which some programs are used to guess and predict passwords and user names to enter the site’s control panel. These programs make thousands and perhaps millions of predictions, which may happen in one of them, entering the WordPress control panel and starting sabotage or exploitative matters within the site. . This usually happens with sites whose administrators use weak passwords, such as “125364” or “a123456,” so these words are easy to guess and your site can be hacked.
Always remember that these hackers have strong and large databases that contain the most used passwords on most sites around the world, and they have the ability to unleash these programs to make predictions that can sometimes reach 100% accuracy for passwords, so do not leave them a loophole in your password. Go to your site’s control panel (in the article we will talk about securing passwords).
The first goal of hackers in this type of attack is to obtain the password and username to enter the WordPress site control panel, so their process begins by launching programs that fetch the login links for hundreds and thousands of WordPress sites, and of course it is easy for these programs to access all sites. WordPress uses the /wp-admin extension to log in to the control panel.

After accessing the link to log in to the site, some information is collected that contributes to predicting the names of the username and password to enter the control panel, where the names of writers, contributors, and users on the site are collected, and their names appear clearly within their articles and contributions to the site, and it is often The username is identical to the member name to log in to the control panel, which makes it very easy to guess the username.
These programs then make thousands of predictions in less than a minute to try to guess the correct login data and begin implementing their sabotage plans within the site.
It is important to pay attention to changing the default login link for the site, because by default the link to the login page is example.com/wp-admin, meaning the site link, then adding wp-admin/ directly after the link.

If the login page for your site is on this direct link that everyone knows, we advise you to change it or allow specific computers to access this page .
What is the impact of brute force attacks on the site?

The victim’s website is affected from the first moment of launching that attack, even if the penetration fails. Here are the most important negative effects that occur on websites that are subjected to a blind force attack:
- From the first moment a brute force attack is launched on the site, the site loads very slowly and the site may crash for a period of time, as a result of hundreds and perhaps thousands of login attempts that are made within the login page in order to try to predict passwords.
- Exhausting your site’s hosting resources if the attack actually succeeds, as hackers run programs that perform some special operations that consume your hosting resources such as RAM, storage space, etc.
- The data of registered members of the site will be stolen if the attack is successful. Your site may be subject to the deletion of all data and files if the attack is successful.
Now that we talked about the brute force attack and how it is implemented on WordPress sites, and the negative effects on the site, we will talk about the most important insurance measures against these types of sabotage attacks.
Protect your site from brute force attacks
Protection against these attacks occurs through 3 stages
- Creating insurance procedures that you can do yourself as insurance behavior on the site without using external tools
- Secure the site using some security add-ons that perform security procedures automatically
- Use additional layers of security by writing some simple code if you want to create higher layers of protection against this type of attack
Now let’s talk about simple actions that any user can do
1 – Do not use login data that is easy to guess

Completely avoid using usernames and passwords that anyone can easily guess. The first step that hackers take in a brute force attack is to assume common usernames and passwords (such as: Admin), so do not leave that opportunity to them.
As an additional security measure, you can log into the WordPress control panel and then go to: Members << All Members . If you have a member registered on the site with the username “Admin,” it is best to delete this membership or change its username and password immediately.

Also among the security measures is that the username to access the WordPress control panel is not the same as the username within the site:
Go to “Edit Profile” and make sure that the login username does not match the username or member on the site. This makes guessing the username indirect and thus adds an additional layer of protection to your site.
2- Use strong passwords
It is important that the password is strong and difficult to guess, by containing letters, symbols, and numbers with more than 8 characters, such as using a password generation tool , as the tool helps you create a strong password through many random experiments.
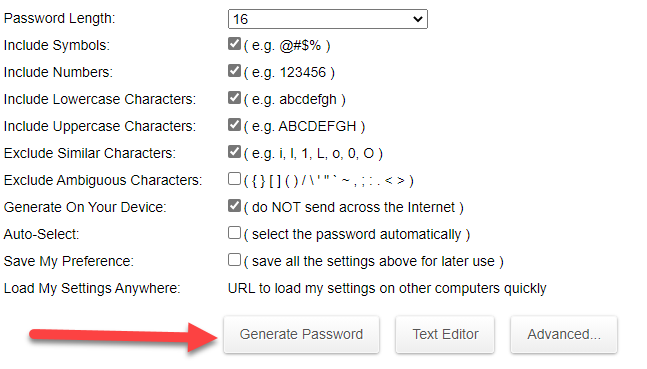
You can click on Generate password to get a strong password. You can take the suggested password and change some letters or symbols in it before actually using it on your site.
Here are some additional tips when creating a password for the login pages on your site, whether for the site manager membership or even the memberships of other users:
- Do not use your personal name, the name of the website or company, or any name that reflects information about or about your business.
- There’s a popular rule of thumb for setting passwords (they should contain uppercase letters, lower case letters, numbers, and special characters like Aw34#$%) so that the word ultimately has no meaning.
- Do not use a short password. Try to increase the number of random symbols, letters, and numbers. The longer the password, the less likely it is to be guessed.
- Do not share the site administrator’s passwords with other people, or through various communication tools.
- You also add strong passwords to the login page of your site, and you must also set strong passwords to access the FTP file transfer manager and the database manager.
When you create a new account for a user, in the “Password” field, WordPress by default gives you recommendations regarding the strength of the password that you type, and if you find a notification stating that the password is “weak or very weak, do not use it or weak, just do not use it.” Try to try a strong password as we explained in the previous paragraphs:

3- Keep your site constantly updated

WordPress is an open source content management system, which means that most of the gaps or weak points that are discovered, programmers work on them and fix them in a very record time, which is what makes WordPress receive continuous updates on a regular basis.
Therefore, keeping your WordPress updated, and certainly also updating your plugins, templates, and the cost of your site’s internal elements, constitutes an additional layer of security to protect your site from vulnerabilities that may exist in old versions of plugins and templates that you install, or even the old WordPress file itself.
4 – Protect the wp-admin file with an additional password
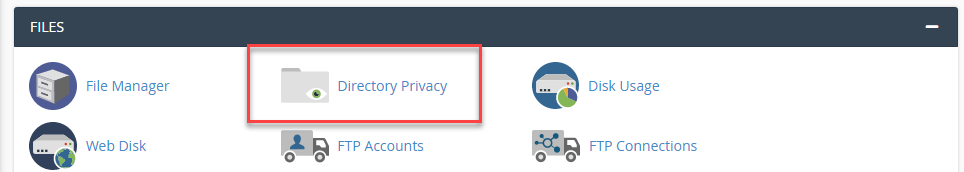
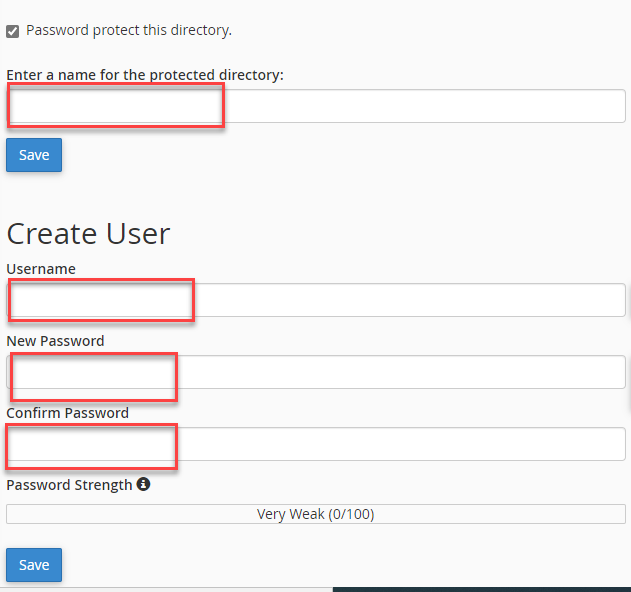
As an additional security step, a password and user name can be set to enter the wp-admin folder, which is located within your site’s file manager. Even if the site is hacked, it will require the hacker to enter a user name and password to enter the wp-admin folder.
To do this security procedure, you can access the site’s control panel (Cpanel) and access Directory privacy:
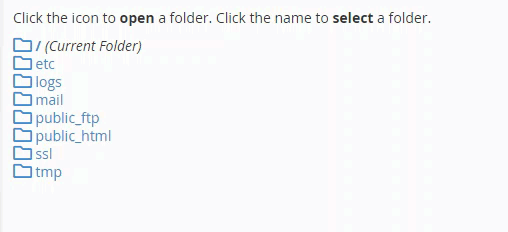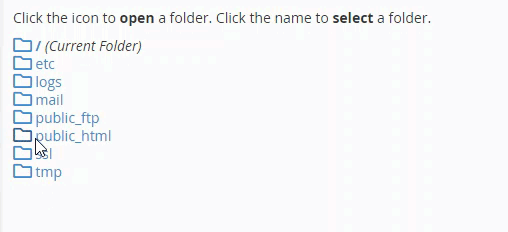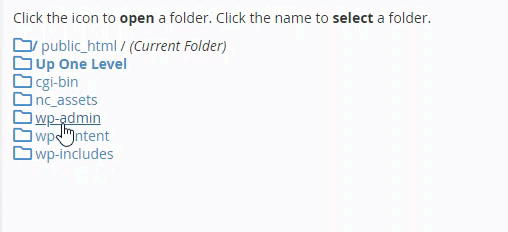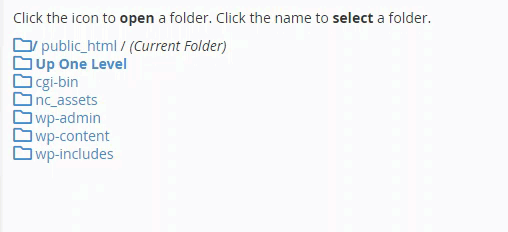
After that, a window will open for you to create a username and password to protect that folder, where you type the name of the folder with a password and username, then click Save :
Use some security additives
After we talked about the steps that can be done manually and directly, let us now talk about some of the security measures that can be performed using some add-ons to increase good security layers to protect against brute force attacks.
1 – Activate two-step verification when logging in
When you activate the two-step verification feature, every time one of the site administrators logs into the WordPress control panel, a message is sent to the site administrator containing a verification code that must be entered in the login window so that users can enter the control panel.
This step adds an additional layer of security to the site. Although it seems a bit complicated as every time you log in you must enter a verification code, it adds a high layer of security to your site.
You can see how to activate two-step verification, which we previously explained in the article on securing and protecting your WordPress website .
2 – Prevent suspicious login attempts

Using the Loginizer add-on, you can prevent suspicious login attempts. It is one of the effective security measures to prevent brute-force attack attempts on the site.
The add-on helps enhance the security of the site by providing many security options, the most important of which is prohibiting entry to people who have exceeded a certain number of failed logins. It is also possible to create a whitelist of IP addresses that are to be allowed only and not all others with the ability to log in to the page. wp-admin, similarly through the add-on you can create a blacklist to block specific IP addresses from logging into the control panel, and many additional security options.
The plugin has more than a million active installations on WordPress sites around the world, and it has regular updates, so it is a good choice for adding layers of security to your site.
After installing and activating the plugin, you can access its settings from within the WordPress control panel. In it, you will find an option for protection from brute force attacks:
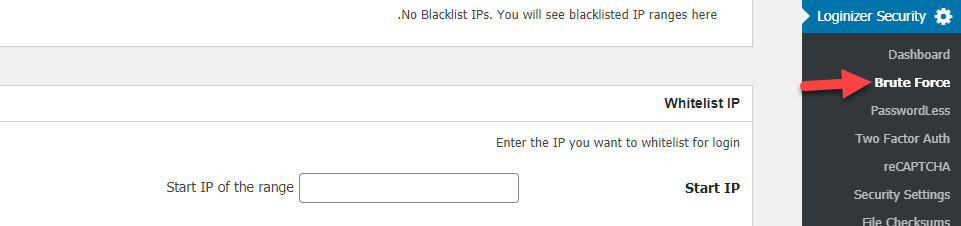
You can browse this window to perform security procedures from Brute Force, where you can customize a white and black list of IP addresses allowed to access the control panel, and you can also specify the maximum number of failed attempts to log in to the control panel after which the login process is blocked, and many more settings Other security options that you can customize from within the add-on settings.
3- Take backup copies periodically
Backing up your site periodically is one of the important insurance issues that you need to take care of. If any damage occurs to your site as a result of a sabotage attack or technical malfunction, there will be a great opportunity to restore the site’s files and data as they were before the damage or malfunction occurred. We recommend that you review the comprehensive guide to taking a backup copy of your WordPress site .
4 – Change the default path to the login page
You can use the WPS Hide login plugin to create another layer of protection for the login page of a WordPress site. As we mentioned previously, it is very easy to predict the link to the login page of any WordPress site, as most login page links end with words such as wp-admin, login, or Admin. .. Which makes it vulnerable to attacks such as blind force attacks and others. You can see how to use the WPs hide login plugin to change the name of the login page in WordPress.
5 – Prohibiting access to site member data
Hackers exploit API codes by accessing: https://example.com/wp-json/wp/v2/users
By replacing exaample.com with the site URL, then the API codes appear in front of them, which contain inside them the usernames of the memberships registered on the site. In this case, the matter is 50% successful in hacking the site by obtaining the username, and password prediction programs begin to work to complete the 50%. Other than the chance of hacking.
Notice the following picture of a site that does not have a layer of protection against showing the API codes that show the names of the site’s membership users:
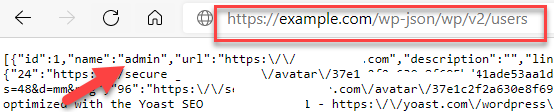
Therefore, we recommend disabling the API codes that display the usernames of the usernames registered on the site, and the Disable REST API extension can be used to hide this sensitive information on your site.
Once the add-on is installed and activated, it prevents the appearance of this sensitive data by default without any additional action from you. Note the site after installing and activating the add-on:
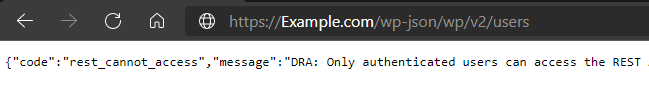
6 – Use integrated protection additives
We advise you to use one of the integrated security add-ons, whether in a free version or a paid version, depending on the needs of your site and the size of your site’s data, such as using the SUCURI add-on, which provides many security options such as: installing a firewall to your site, which in turn greatly enhances the security and protection of the site, and also provides Alerts system if any suspicious action or unusual registration process occurs on the site.
Advanced insurance procedures
In this part, we review some of the security procedures that can be done by modifying the .htaccess file located in the WordPress file manager, in order to greatly customize many of the site’s security options. These procedures are as follows:
1 – Prevent the feature of browsing the site’s files
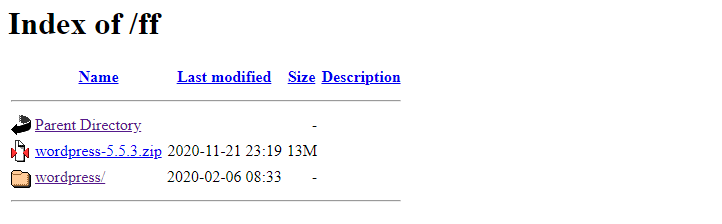
If you have a folder inside your site that does not contain an index page, Index.php or index.html, and so on.. it is easy to review the files that are inside that folder by typing the folder path in the link inside the browser, and all the files that are inside it will be reviewed, Which may include files containing confidential or sensitive data.
htaccess file. You can completely cancel this file browsing feature by entering the file and typing the following command:
2 – Prohibiting the running of .php programs within some paths
It is known that WordPress is a content management system based on the PHP language, which is used to implement most of the programming commands that take place within the site or are done by connecting to databases . Therefore, php codes cannot be blocked in most WordPress files.
Hackers use this language’s programs, which are implanted inside WordPress files and various folders in order to implement their sabotage commands, after you are able to hack the site and enter the file manager.
As a precautionary measure, we cannot confirm that it will be 100% effective, but it can protect your site from some risks. It is to block the running of .php programs in some paths that do not require running php codes, such as the Uploads folder.
To block php code from running inside the Uploads folder, you can go to the Wp-content/uploads directory and then create a new txt file named htaccess. Without putting any extension after its name, then paste the following code into it and save:
deny from all
Conclusion
There are many website owners who do not pay enough attention to securing the site until they are exposed to a hacking or piracy incident that causes them a lot of serious damage. Although WordPress is considered an open source content management system and is largely secured by the programmers involved in its development, there are Some actions that you must take on your part to increase the security of the site and thwart all attempts by saboteurs and pirates.
This includes all security measures, starting from setting strong passwords, not making access to site user data easy, as well as securing the site using one of the security add-ons designated for that. These are all security measures that you take on your part in order to enhance the security and protection of your site not only against power attacks. Blind brute force attack but against any other attacks
































Leave a Reply