Website hacking is very possible because there are many software vulnerabilities in websites that are usually exploited by hackers. Especially the security vulnerabilities caused by the site administrator, such as: weak passwords, the use of common words that are easy to predict, or other vulnerabilities.
In our article today, we will try to clarify these vulnerabilities, and explain how to avoid them to protect your site from being hacked. Most importantly, we will explain the most common methods that hackers use to carry out site hacking operations so that you can try to avoid them and protect your site from falling victim to these methods.
We will also explain to you how to monitor your site moment by moment and know if it has been hacked without you noticing it, as the hacker sometimes relies on hiding himself and his destructive effects from the site administrator and not revealing the effect of viruses on him.
Fortunately, it is relatively easy to provide the necessary protection for WordPress websites, as there are several plugins and techniques that make it easier for you to do this. All you have to do is read the article and choose the method that suits you.
How do you know that your site has been hacked?
There are several ways to help you monitor the status of your website, monitor its performance, and find out if it has been hacked or has a virus or sabotage program running in secret without you noticing it.
Below we will review the most prominent of these methods.
1- Through a web browser
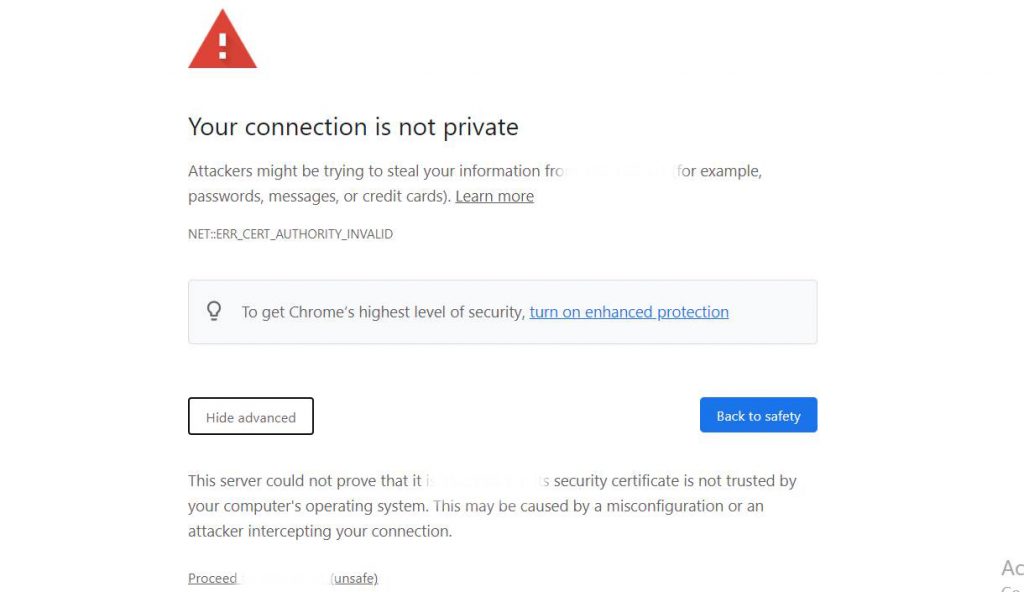
The easiest and simplest way to know if your site has been hacked or not is through a web browser. All you have to do is enter your site through private browsing mode, and try to open the site. If you see a message: This site is a phishing attack, then you will know that your site has been hacked and that the hacker is trying to extract the data of the visitors who They access your site.
NB :
You may see a message, “Your connection is not private,” which is completely different from the message that appears if the sites we mentioned are hacked (Phishing attack ahead), because it appears because the site’s SSL certificate has expired or has not been added to it, and it does not necessarily mean that the site It has been hacked. So if you find this message, first check your SSL certificate, its expiration date, and that it is working properly.
2- Via Google Console
One of the most popular ways to detect website hacking is to use the Search Console service from Google. This service is a free service that enables you to monitor your website’s results in search engines. It provides you with a detailed view of your website’s performance in search results, its performance, and the speed of its pages.
Through this service, you can also follow up on technical problems on the site (including hacking, virus infection, or spyware). Google sends you a warning if any suspicious activity appears on the site, a technical malfunction occurs, or any virus or malicious software is found on it.
Use Google Console to check if the site has been hacked
1.You must first register your site in the Google Console service, and here you will find a complete explanation of how to register in Search Console .
2. Of course, problems will not appear to you immediately after registration, but the examination will be done within days. If any problems are discovered, you will be notified via email.
3. To find out the security problems on your site, go to Google Console, then scroll to the bottom of the side menu until you find the Security section (Security and Manual Action).

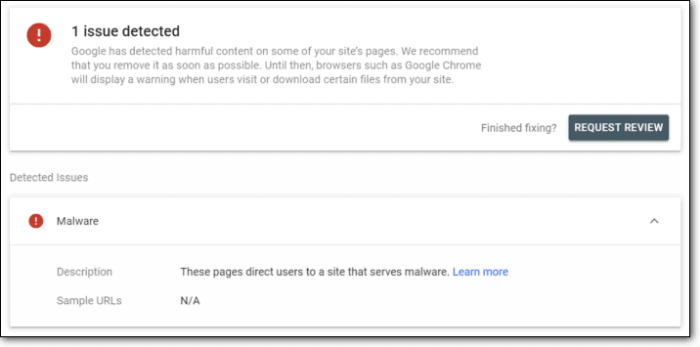
4. Open the Security Issues tab to show you whether there is malware running on your site or not.
5. If your site has been hacked, a message similar to the following will appear:
3- Strange advertisements appear on the site or you are redirected to another site
Most hacks aim to gain revenue by displaying ads on your site. But in most cases, these ads will not appear to you as a website owner, as hackers often rely on software that hides the ads from you if you log in to the site, and only shows them to visitors who are not logged in. Thus, you will not see these ads if you are the site administrator, and you will not suspect that it has been hacked!
To check whether there are additional advertisements on your site or not? You must access the site from an incognito browser. It is also preferable to detect this situation through Google search and not through the website link directly, as some rely on showing ads to visitors from Google or Facebook only.
If you find any strange ads or pop-up ads, make sure there is a virus on the site and it has been hacked.
The hacker can also redirect your entire site to another site, which leads to the loss of all your visits. You can discover the matter early if you track site visits through the Google Analytics service , as it helps you know the activity of visitors on your site at the present time, such as their number and the pages they visit. They are browsing it and also the type of device used to browse your site.
4-By checking your site on security platforms
You can also find out whether your site has been hacked or not and whether it contains spyware (malware) or viruses of any kind by using specialized site scanning platforms.
For example, sucuri.net is a site that conducts a comprehensive security check of your site to find out how protected it is, and whether it contains any malicious files, in addition to evaluating the site and finding out whether it is placed on ban lists around the world or not.
For example, we checked our WordPress site through this site and got the following result:
As you can see in the scan result, our site is safe as it is free of any viruses or malicious files. The check also shows that the site is not on any blacklist.
The protection on site is also high. The closer the result on the sliding bar is to the minimum value (Minimal), the stronger the protection is for the site, and the closer it is to the maximum value (Critical), this means that your site’s protection is weak and it may contain malicious files and dangerous security vulnerabilities!
You can also try checking your own site from the following link: sitecheck.sucuri.net
What to do if your site is hacked?
If you examine your site and find that one of the previous problems appears within the site, and you confirm that the site has indeed been hacked, in this case you must follow a series of steps in order to be able to remove any harmful files or viruses from the site.
The most important of these steps is to know the source of the virus, and because this is almost impossible, you can resort to cleaning viruses from all places that might be the reason for the virus to reach your site. Below we guide you to the most important steps that must be followed once you confirm that your site has been hacked.
1- Ensure that all your devices are free of viruses
The virus may be present on your computer and transfer your site and hosting data to the hacker, which in turn leads to your site being hacked and being able to plant viruses or spyware inside it, so we advise you to check all the devices through which you have accessed it.
You can do this by logging into the site or hosting, and you can scan the malicious files on these devices with an anti-virus program. Such as Malwarebytes , which is one of the best programs for scanning malicious files on the computer and which is recommended by most hosts.
2- Change the website’s passwords and increase its protection
After ensuring that your computer is free of harmful files. You must log in to the hosting and change all data for accessing the site. Such as cPanel login data, as well as FTP data and any control panel that may be available for logging in. Including your database password.
After that, activate the two-step registration method (two-factor authentication) on your site by confirming the login using the phone number to increase the protection of your hosting, as we will explain shortly.
To ensure that no one accesses your hosting without permission. You must choose a strong and difficult password that is long, and consists of upper and lower case letters, numbers, symbols, and punctuation marks. Or you can simply use strong automatic password generation platforms like lastpass.com .
3- Restore the last backup before the virus appeared
Log in to the hosting, delete the current site with all its files and restore the last available backup before the hacking problem appeared on the site. Through this, you can completely delete the virus.
But what to do if you don’t have any backup?
In this case, you need to write to hosting support and ask them about the backups they have available. Most hosts provide the feature of restoring backups even if you have deleted all the copies you have, or have not subscribed to the automatic backup service before.
But it should be noted that this service will mostly be paid. Hosting helps you restore one of the backup copies for a price of $25 in most hosts, and this price may change from one host to another depending on the type of hosting subscribed to. Once you restore the backup, change your wp-admin password immediately. With this, you will have restored your site again and it will return to work without any problems.
What methods do hackers use?
Most of the time, hackers rely on malicious software that is installed in templates or hacked add-ons that are downloaded from the Internet without a license from its original programmer, and which are widely spread on the Internet.
These additions are decrypted and made available for free to everyone. These templates and add-ons are often packed with malicious files to control your hosting or benefit from the site in any way. Your site can also be hacked through the devices you log in with if there are any malicious files present on those devices, and many other methods that we will discuss shortly in the following paragraphs.
1- Phishing
This technique relies on sending malicious files through your email. The hacker assumes the identity of any of the giant companies that you deal with, such as Amazon, YouTube, or any company that you have dealt with through your email, and then sends a link containing a malicious file.
Once you click on this file and download it to your computer, the malware file will be installed, which unfortunately means access to all your data on the computer, including your website data!

This method is used in most of the famous hacking operations, whether for WordPress sites or any other site, as the method aims to penetrate the site administrator’s device and thus access all the site’s data. Therefore, you must be careful not to click on any link in your email without verifying the source of this email and the identity of its sender. . In general, it is not recommended to open links about which you are suspicious on the personal computer that you use to access your site.
2- Malicious software found in plugins and templates
Malware is added to most add-ons, paid programs, and is freely available on the Internet. Which prompts many beginners to download it and add it to their WordPress sites, and thus sites and hosts are hacked very easily. Therefore, before downloading any add-on or template, you must make sure that you are downloading from the official website. This method is the most common method for hacking WordPress sites, especially beginners’ sites.
3- Techniques for hacking non-targeted websites
These techniques do not target your site itself, but rather target security vulnerabilities in the WordPress system as a whole. In other words, it targets sites that rely on content management systems in general, and WordPress sites in particular, given that they are the most widespread and popular on the Internet.
This method relies on targeting a security vulnerability in one of the versions of the WordPress system, where the hacker develops a mechanism to search for all sites running this version, and then tries to hack it through this vulnerability.
One of the examples that caused a client’s website to be hacked was due to the automatic installation of WordPress through cPanel. The site was hacked only a few hours after it was installed because the default password for WordPress was left unchanged during the installation process, which was pass, and the hack was only done because of my delay in changing the password.
This vulnerability has been exploited to access all WordPress sites whose password matches the word pass. Therefore, it is recommended to change the password before installation. For this reason, most hosts are currently moving towards not adopting automatic passwords, and forcing you to type a strong password during WordPress installation.
How to protect your WordPress site from hacking
Prevention is always more important than cure, which is why you must be careful to protect your site from hacking before it happens. This is done by ensuring that a set of basic matters are taken into account in your WordPress site to ensure its protection from any possible hacking attempt. Below we explain to you the most important of these basics.
1- Ensure that WordPress, plugins, and templates are updated to the latest version
You must monitor the version of WordPress and your plugins, update them regularly, or activate automatic updating for them. In order to make sure that you actually have the latest version, and to know whether your site’s version of WordPress needs to be updated or not, go to your site’s WordPress control panel > then go to the Updates tab as shown in the following image.

Through the WordPress Updates page, it will appear to us that our site has already received the latest available update, which is at the time of publishing this article (version 5.8.1).
In order to find the add-ons that need to be updated on the same page as previous updates, scroll to the bottom of the window and a list of all add-ons that need to be updated will appear. Select them completely, then click the Update button.

Then scroll to the bottom of the window, to show you the templates that need to be updated. Follow the same previous steps to update the template used on your site.
With clarification thatIt has become possible in WordPress to activate the automatic update feature for templates and plugins, as you will automatically receive the latest version as soon as it is available. To activate this feature, go to the add-ons page on your site. Next to each add-on, you will find the option (Activate automatic updates). Click on it to activate the automatic update for this add-on.

2- Add a firewall to your site
One of the most important steps to protecting a WordPress site is by adding a second step of protection by adding a firewall, which helps you confront all hacking attempts and attacks before they reach your site. Adding Wordfence is one of the best plugins used to protect your site and create a strong firewall for free on the site. your.
3- Disable the file editor located on the wp-admin page
This option is very important, because if any hacker gains access to your WordPress site’s control panel, he will not be able to add code to the site through the feature of editing template codes and plugins that WordPress provides through the site’s control panel.
Therefore, it is important to turn off this feature so that the hacker cannot redirect your site to any other site, add advertising codes within the site, or even stop your entire site from working. You can turn off this feature by logging into your hosting control panel ( CPanel ), then going to the file manager.
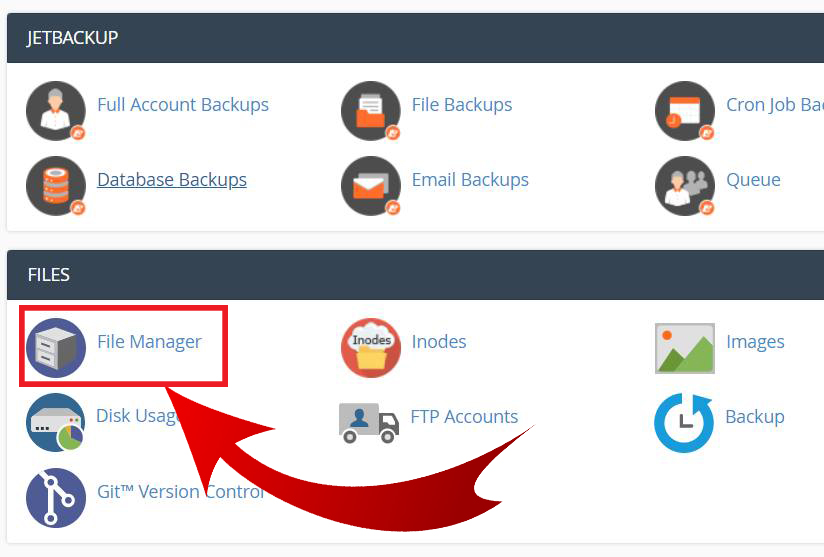
Then choose where to save the site files. If you have one site on the hosting, the files will most likely be saved in the (public_html) folder.
Open the folder and all your site’s files will appear. Scroll down and search for the file wp-config.php. After finding the file, click on it with the right mouse button. A menu will appear from which choose the (edit) option to edit the file.
A new window will open in your browser to edit the wp-config.php file. Go to the end of the file and add the following code at the end.

Then save the changes by clicking the save changes button at the top of the page, and thus you have stopped the file editor of the template.
4- Add two-step verification during login
The last step of protection we use in this article is by adding two-factor authentication, which requires the user to log in with two steps. The first step is through email and password as usual, and the second step is through your mobile phone through the Authenticator app by Lastpass. Thus, you will not be able to log in except through the code inside the application, even if you have the password and email.
To activate this feature, follow these steps:
1. Go to the add-ons page and choose Add New> and then search for the add-on Two Factor Authentication

2. After you find the required add-on, Two Factor Authentication, click on the Install Now button next to its name.

3. After installation, a page containing a QR code will appear in front of you, as shown in the following image.

4. You must install the LastPass Authenticator application on your mobile phone from here: for Android | For iPhone
After installation, open the application and click the Add New button or the plus sign at the bottom of the application
6. The barcode reader (QR code) will open for you. Point the camera at the code appearing on the screen and the two-step verification feature will be activated directly.
7. Now you will only be able to log in using the variable code that appears for only 30 seconds and then changes automatically on the application.
Read also: Change the wp-admin login page link for WordPress and activate reCAPTCHA
Thus, you have learned about the most common ways to hack a WordPress website and how to protect against them. You can also learn more about the procedures and methods to secure and protect your WordPress site by reading the following article.
Conclusion
After we learned about the most common methods of hacking WordPress sites, and how to protect against them. We must remind you that the most important factor in hacking WordPress sites are errors caused by the site owner himself, whether through hacking by phishing or through installing cracked plugins or templates. Therefore, we advise you to verify all plugins and templates before installing them.
To avoid hacking your site by any of the methods we mentioned, you must ensure that the site’s add-ons are constantly updated, while monitoring your site, its visits, and the software problems found on it through Google Search Console, as we mentioned to you, to ensure your site is protected from hacking. Remember, an ounce of prevention is worth a pound of cure.
At the end of our article, we would like you to share your experience with us in the comments and tell us: Has your site been hacked before? Have you ever faced one of the problems we mentioned in our article? If you have experienced it or are still suffering from the problem of your site being hacked, you can write to us and specify the problem you are facing in the comments to help solve it.
































Leave a Reply