Website owners pay great attention to databases and their protection, since they contain all the basic data of the website, including complete customer data and financial details of the website. They also play an important role in determining site performance and stability.
If the site has recently been exposed to malware, or unusual activity has been observed, this may be the result of databases being compromised/malicious files. Therefore, it is recommended to scan databases and delete malicious codes, either manually or using specialized protection tools, and in this article we will explain the two methods in detail.
How can a WordPress database be hacked?
WordPress databases are hacked using several basic methods, as follows:
1- Database injection – SQL Injection
WordPress sites provide users with a variety of data entry fields, such as fields for writing comments on articles, filling out surveys, contact forms, and others. This data is stored in the site’s databases.
Not securing data fields and programming them efficiently can pose a security risk. For example, if data is not validated to reject numbers in fields that are not intended for them, or to verify the format of an email, or prevent the insertion of external links into text fields, attackers can exploit these vulnerabilities to inject malicious code into databases , exposing them to… to the risk of hacking.
2- Brute Force Attacks
Brute Force Attacks refer to the strategy that hackers rely on to guess the username and password used to access the main control panel. These attacks are carried out by making millions of automated attempts.
When the username and password are guessed correctly, the attacker gains access to the main control panel, and thus access the databases. Therefore, it is always preferable to use relatively complex usernames and passwords, which include a set of unexpected symbols, to make the guessing process very difficult.
3- Not updating add-ons and templates
The weak points of WordPress websites are often represented by plugins and templates, especially since WordPress is considered an open source platform and has several plugins and templates available, whether through the internal or external store, and they are uploaded unreviewed on the platform.
As a result, plugins and themes can be poorly programmed in terms of security, causing hackers to look for security vulnerabilities in them with the aim of exploiting them to hack WordPress sites. Through this hack, databases can be accessed.
Developers always provide updates to plugins and themes to enhance security and patch any vulnerabilities. Therefore, you should always consider updating add-ons and templates to the latest versions, and obtain them from the official source to ensure obtaining secure and reliable versions.
The same applies to updating the WordPress system itself to the latest version, as all security vulnerabilities in older versions are closed and improved.
For example, the Ninja Form add-on previously included a security vulnerability that hackers exploited, based on a report published by the Wphackedhelp website , where an existing contact form was replaced with another malicious contact form, which helped inject malicious SQL files into databases, but the vulnerability was improved in updates. suffix, and the same applies to the Convert Plus add-on as well.
4- Use an FTP connection to transfer data
Hosting companies provide several ways to connect to the server, the most important of which is an FTP connection , an SSH connection , or an SFTP connection. If you rely on an FTP connection, the server data is transferred using the username and password via an unencrypted connection.
Therefore, hackers may take advantage of your connection to the server via FTP, allowing them to spy on server data and steal information. With this data, they can have full control over the server. Therefore, care must always be taken when connecting to the server and transferring files, and it is preferable to rely on an SSH connection or an encrypted SFTP connection, as the SSH and SFTP connection provide an additional layer of security by encrypting data during transfer, which makes it difficult for attackers to use the data in unauthorized ways. Authorized.
Checking WordPress databases
First, you must completely scan your site files for malicious files and clean the site from all harmful effects, because malicious files can be transferred again from the site files to the databases after they are cleaned.
You must also take a backup copy of the WordPress databases and site files before checking or modifying the databases, so that you can return to them in the event of an error in dealing with the databases.
Manually scan WordPress databases
1- Export WordPress databases
Hackers rely on some custom PHP functions and commands for WordPress to access databases. Therefore, it is preferable to search within databases for the most common of these commands. If these commands are present within databases, this is a high indicator of a database breach. You can also look for external links or iFrames appearing within the site as an additional sign of a possible hack.
You must first export your WordPress database as a text file to enable searching within it. You can do this by entering the main hosting control panel, then heading to the databases. The method varies slightly depending on the hosting company, but in general you can find an option to export the database as a text file, and then choose the database for your WordPress site from the side menu:
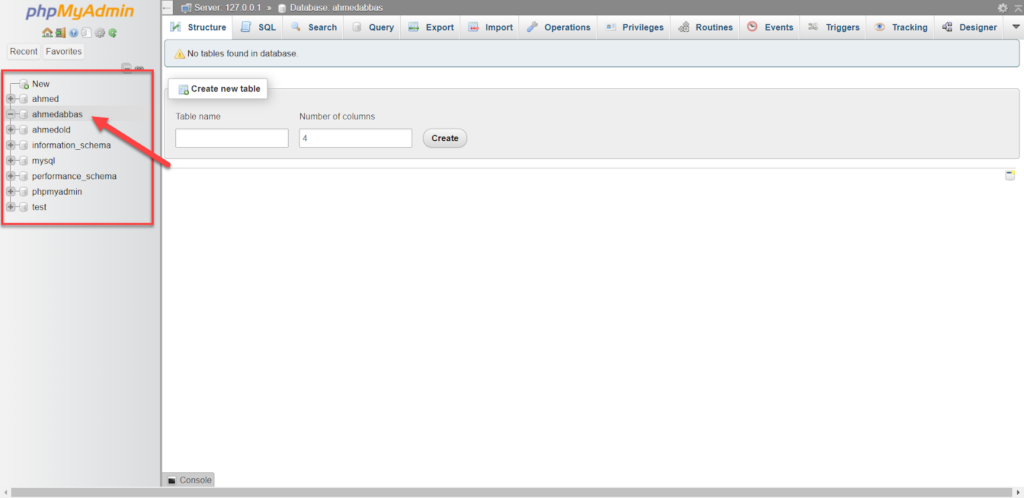
After that, you choose Export from the top menu, then choose the Quick export method from the Export Method option , then select the SQL formula from the Format option, then click on Export as shown in the following image:
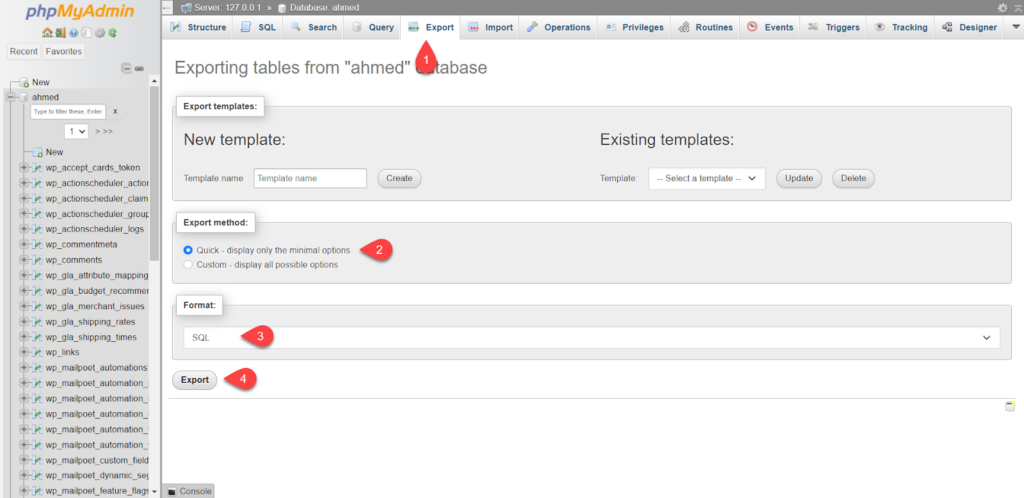
The WordPress databases will now be loaded, and you will open the file with Notepad to search for inappropriate functions and commands.
2- Search for inappropriate PHP functions and commands
You start by searching for the most important PHP functions and commands that hackers rely on. The most important of these functions are the following:
- base64_decode : The base64_decode command is used to decode data encrypted using base64 encoding. WordPress is an open source system that is not encrypted, so databases should not contain a base64_decode command. If it is found, it indicates the presence of an encrypted file that is processed with this command, so you search for a command. “base64_decode(” or “base64_decode(”) command
- gzinflate : The gzinflate command is used to decompress encrypted files also based on a special code. Also, the WordPress system should not contain encrypted files, so you search for the “gzinflate(” command or the “gzinflate(” command)
- eval : The eval command is used to treat a custom command as a valid command even if it is illegal or illegal. Programmers do not prefer to rely on this command completely, so if this command is found, it may indicate the presence of a malicious file classified as a valid file, so you search for the “eval” command. (“” or “eval(”) command
- error_reporting(0) : The error_reporting(0) command is used to hide code errors, and thus the system error reports are incorrect, which helps hackers hide the results of malicious files, so you should search for the “error_reporting(0)” or “error_reporting (0)” command.
- shell_exec : The shell_exec command is used to execute a command at the entire server level, and this is the primary goal of hackers, so you search for the “shell_exec(” command or the “shell_exec(” command)
- globals : All globals commands pose a security risk in the PHP system and may be used to hack the site. Therefore, they have been removed from all versions of PHP since the release of PHP 4.2. Therefore, you must search for globals commands, identify the plugins that depend on them, and then remove them completely from the WordPress system.
There are several other PHP functions and commands that hackers rely on, but the previous list is the most commonly used functions. It is worth noting that the presence of these functions does not always indicate the presence of a hacking situation, but programmers can rely on them to implement certain functions, so the matter must be carefully examined before dealing. With him.
3- Search for unknown links or iframes
Attackers embed external conversion links or iframes into WordPress, trying to hide them to avoid detection by site owners. Therefore, you should search the database for functions related to the iframe, reviewing all results related to the site to check whether they are actually linked to the site or if there are results that point to unfamiliar links that are not appropriate for the site’s content.
In the same way, you search for external links if they appear on the pages of your site, or your site is redirected to them, in order to determine the source of those links. You can also examine your site’s code for unknown links or iframes.
It may require some programming experience in dealing with databases, and determining whether the commands are used normally or if they harm the site. If you do not have sufficient programming experience, you can hire a professional freelancer by relying on WordPress services .
Manually scan and clean WordPress databases
If you find matches of inappropriate PHP functions and commands on WordPress databases while searching, or unknown links or iframes, this is a big indicator that there are malicious files in your databases, and you need to clean them.
You can clean up WordPress databases manually, but you must be careful and have some technical experience, as dealing with databases requires precision and attention to detail. Incorrect manipulation of data may cause some problems to appear on the site, cause it to malfunction or stop working completely, or even stop the site suddenly.
Therefore, if you have a previous backup copy of the databases before being hacked, you can rely on it, but if you do not have a backup copy, or it is not up to date, you can search for inappropriate commands and remove them manually.
So you access the WordPress databases again, then choose Search from the top menu, as shown in the following image:
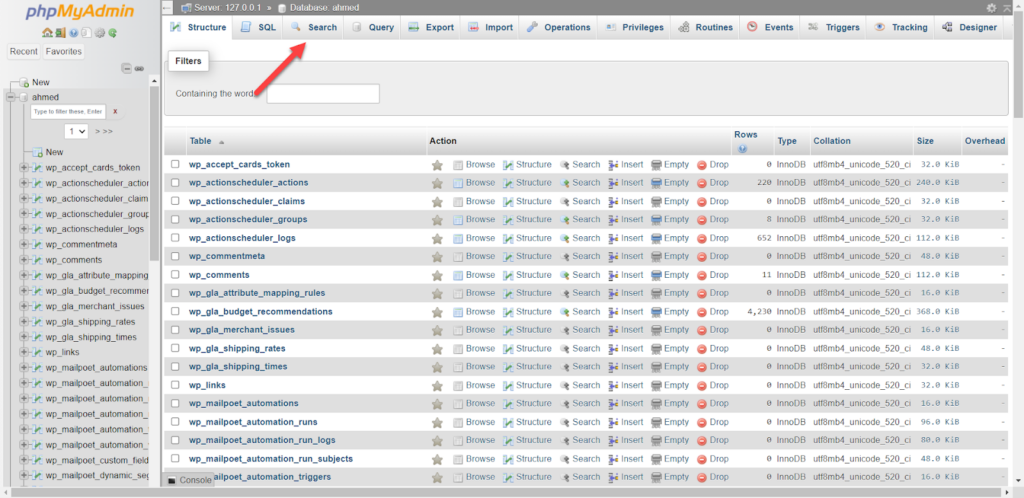
After that, you set the following options:
- Writing inappropriate PHP functions, commands, or links in databases.
- Select at least one of the words option from the Find tab .
- Select all database tables from the Inside tables tab , by clicking Select all .
After that, you press Go, as shown in the following image:
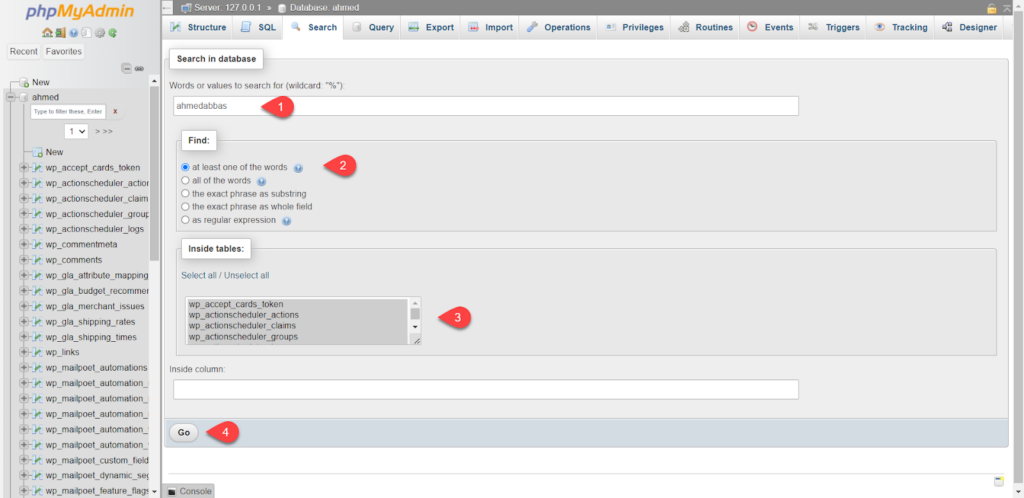
You will now see matching results in all database tables. You select the matching results, then press Delete directly to delete, or Browse to preview and examine the result before canceling, as shown in the following image:
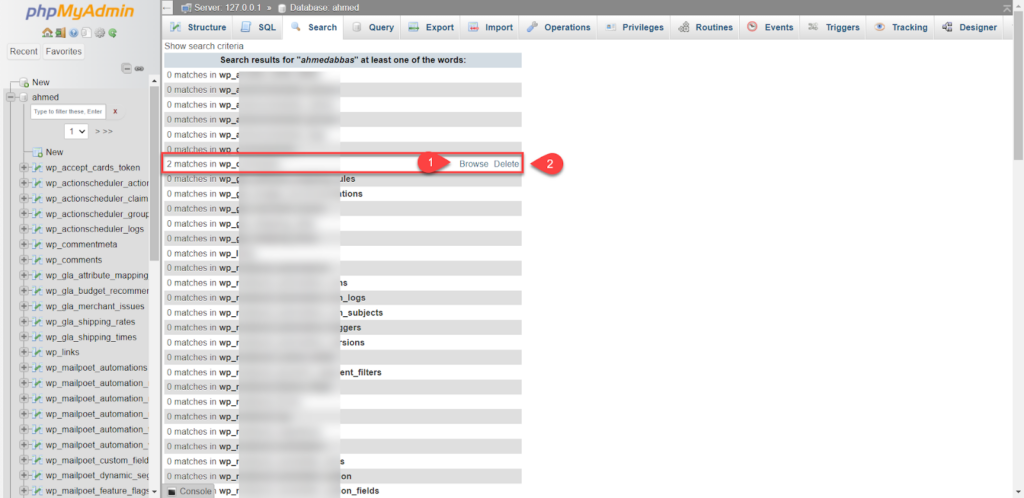
You now repeat the previous step for all the results you obtained from scanning the databases, gradually removing the files.
Scanning and cleaning WordPress databases using security plugins
The other solution for cleaning WordPress databases is to rely on WordPress protection plugins, especially since they do not require technical expertise as in the manual method, but it may require an additional cost to remove malicious files.
There are multiple protection options for WordPress, and they differ in terms of the way they deal with databases. The best of these options are the following:
- MalCare.
- All In One WP Security & Firewall.
- Wordfence.
- Juices
1- MalCare : The MalCare add-on helps you scan your entire site files, in addition to the databases, in search of malicious files or codes, thus ensuring that malicious files are not transferred from the site files to the databases again. When the MalCare plugin scans your site’s databases, it will only provide you with a report on the number of malicious files, but you will not be able to view the location or details of the malicious files or use the automatic scanning tool for them unless you upgrade to the paid plan.
2- All In One WP Security : Addition helps youAll In One W P Security Several protection tools scan site files and databases by relying on the DB Scanner tool in search of malicious files or codes, in order to prevent harmful files from transferring from site files to databases again. It also provides you with the DB Backup tool to automatically save a backup copy of databases, as well as the DB Prefix tool to change the prefix of database tables, thus reducing the risk of SQL file injection, the main cause of database hacking.
3- Wordfence : helpsAdd WordfenceIt scans site files and databases to automatically detect the presence of any security threats or malicious files, while providing a firewall that prevents SQL injection attacks and hacking attempts, and responds to Brute Force attacks. Through the Wordfence Care service, the necessary support and services are provided through the Wordfence team to manually clean databases after they are hacked.
4- Sucuri : The Sucuri add-on helps protect WordPress sites from security threats and hacking. The add-on automatically scans site files and databases for malicious files or security threats in the entire system. In addition, Sucuri provides an advanced firewall that helps prevent SQL injection into databases, Brute Force attacks, and the inclusion of files on the server through RFI communication services.
Conclusion
If your site’s databases are hacked or SQL files are injected, you may not notice the impact quickly or the hacker may hide all traces of the hack, but the result can quickly appear in search engine results.
Therefore, you must periodically scan your site’s databases for malicious files or codes, and the previous steps will be sufficient to scan databases based on the most important PHP functions and commands that are common to hackers.
If you do not have sufficient technical experience, you can rely on security plugins to automatically scan and clean WordPress databases, but this will certainly come at an additional financial cost.
Databases must also be secured by changing the prefix of database tables to avoid injecting SQL files, and relying on a strong firewall to confront Brute Force Attacks, taking into account keeping a periodic backup copy of the databases, in addition to relying on reliable add-ons and updating them periodically to the latest version of them. This is to avoid hacking databases in the first place.
































Leave a Reply